Due to the occurrence of various hacks targeting DeFi protocols, wallets, and centralized exchanges, the security of digital assets has emerged as a paramount concern for users. While owning private keys is essential, it is not sufficient to ensure the safety of one’s crypto assets, especially considering that the wallet itself stores and utilizes the private key. In this article, we will delve into the principles and approaches we adhere to in the design and development of our white-label wallet solution, emphasizing the importance of transparency and understanding for users.
The Pervasive Nature of Wallet Breaches
Wallet breaches in the Web3 space have reached alarming proportions. According to a study by Beosin EagleEye platform, intentional attacks resulted in the loss of nearly $0.5 billion worth of crypto assets in the first half of 2023. Wallet and crypto exchange attacks accounted for significant losses, with approximately $78.2 million and $50.1 million, respectively, in H1 2022.
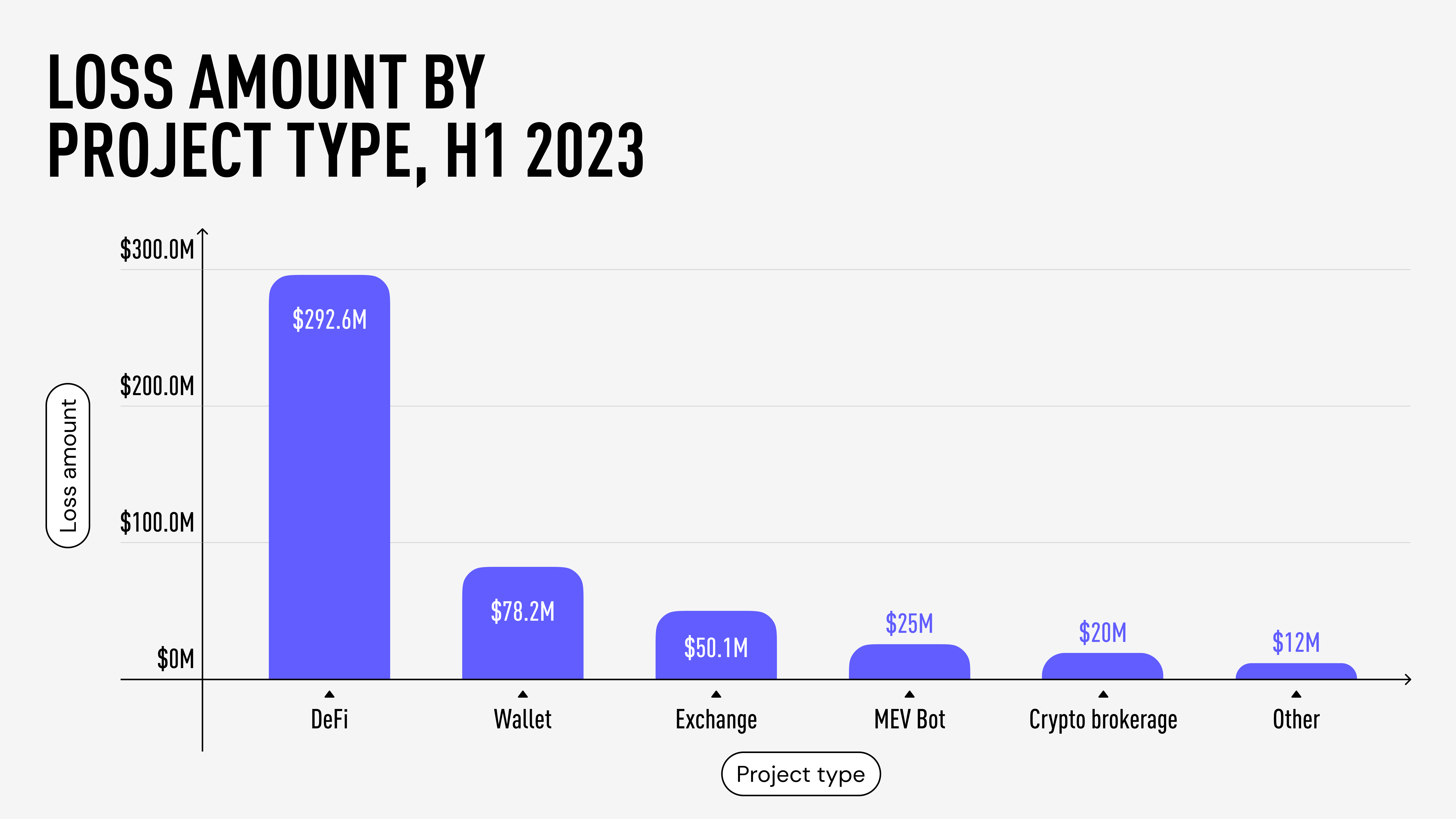
Such breaches often have a mass-scale impact, as vulnerabilities can be exploited for all users of a particular wallet or platform. For instance, the Slope Wallet Hack has probably compromised the private keys of any user who had ever used their application. This is why when examining the largest breaches surpassing $10 million in H1 2023, 50% of top hacks involved custodial and self-custodial wallets.
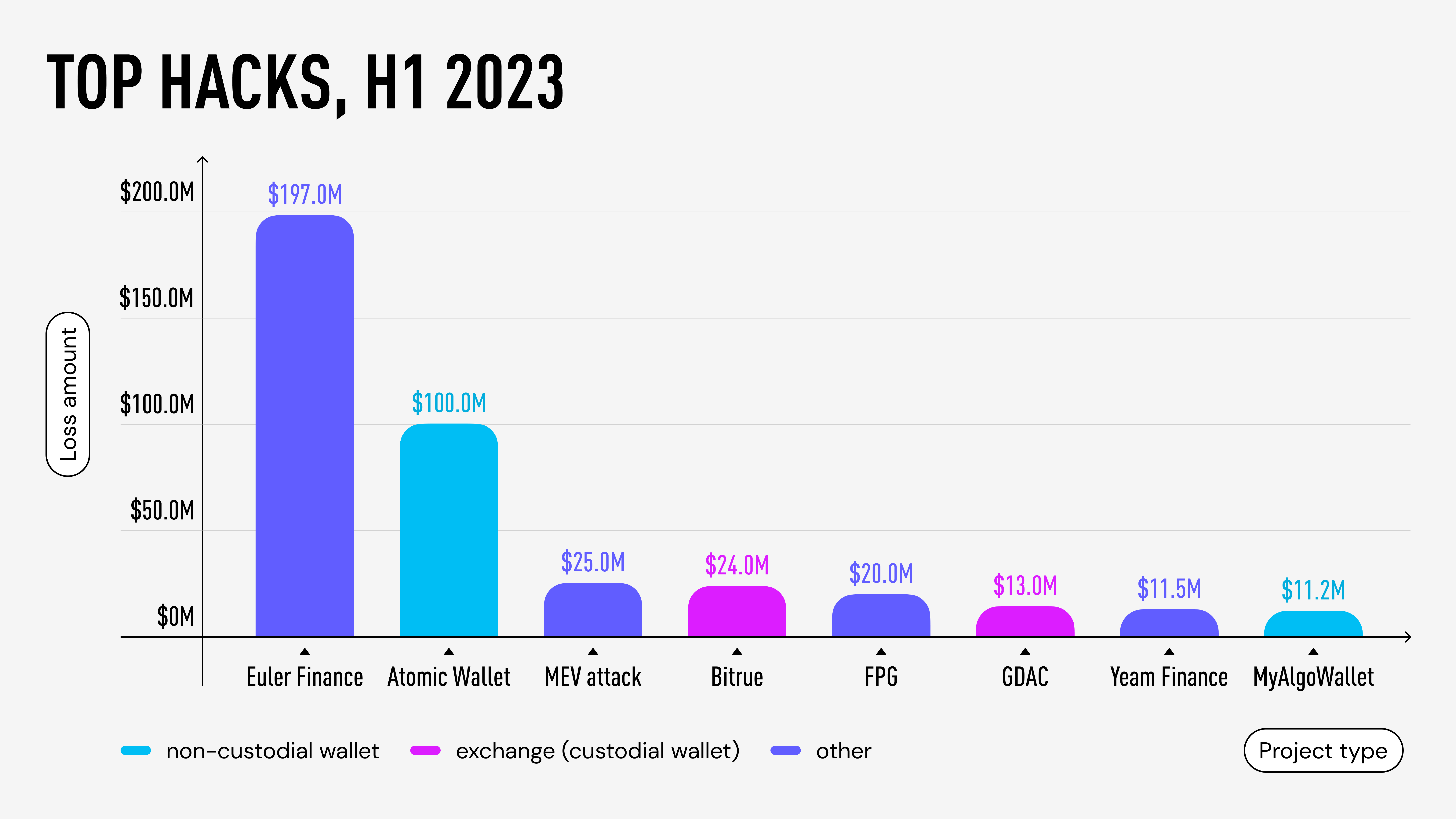
Security Principles of Wallet Development
To ensure the security of self-custodial wallets, we adhere to the following principles. While these measures cannot guarantee 100% security (nothing can), they promote transparency and openness to our audience while inviting contributions from blockchain experts and enthusiasts.
Device-Based Generation of Private Keys
One of the fundamental aspects of wallet security is the generation and management of mnemonic phrases and private keys. Our wallet ensures that the mnemonic phrase and all derived private keys never leave the user’s device. This means that the generation of the mnemonic phrase and computation of private keys happen exclusively within the client-side application, be it on iOS, Android, or a Web Extension. Additionally, transaction signing with the private key is also confined to the client side. By keeping these processes within the user’s device, we mitigate the risk of exposing sensitive information.
Open Source Wallet Core
The core encompasses mnemonic generation, derivation of public and private keys, transaction formation, and signing. Our wallet core is developed using Kotlin, Swift, and TypeScript programming languages and is publicly available. Such transparency allows users to verify our security measures and propose improvements, ensuring that our wallet core remains resistant to emerging threats.
Interoperability through Blockchain Standards
Wallet compatibility is achieved by adhering to widely accepted blockchain standards: BIP32, BIP39, and BIP44. These standards define how wallets derive private and public keys, generate mnemonic phrases, and establish a logical hierarchy for deterministic wallets. By utilizing these standards, our users can export their mnemonic phrases and transition to other wallets that support the same standards. Likewise, users of other wallets adhering to these standards can import their mnemonic into our wallet. This interoperability empowers users and ensures they are not locked into a single wallet provider.
Furthermore, adhering to these standards enables Bitcoin and similar blockchains to generate a different crypto address for each transaction input and change output, thereby enhancing user anonymity (as seen in the UTXO model). However, many crypto wallets, including TrustWallet, do not support this feature.
Genuine Random Generation
It is essential to generate mnemonics based on a sufficient length of entropy, which represents randomness. By adhering to this principle, the number of possible mnemonics becomes astronomically large, making brute-force attacks impractical.
For instance, according to research conducted by Ledger Labs, certain TrustWallet’s web extension versions suffered from a vulnerability where the entropy was only 32 bits, resulting in approximately 2³² or ~4 billion possible mnemonics. Exploiting this weakness, an attacker could have potentially compromised around $30 million. In contrast, our wallets utilize 160-bit entropy, offering 2¹⁶⁰ different mnemonic combinations, rendering brute-force attacks computationally infeasible:
2³² = 4,294,967,296 possible mnemonics
2¹⁶⁰ = 1,461,501,637,330,902,918,203,684,832,716,283,019,655,932,542,976 possible mnemonics
To prevent adversaries from replicating entropy, wallets must employ truly random number generation. We rely on well-established system libraries provided by operating systems to generate random values. Additionally, we subject our entropy to the NIST SP 800–22 statistical test suite for the Validation of Random Number Generators, ensuring its randomness aligns with cryptographic standards.
Industry-Wide Security Standards
We adhere to the Open Web Application Security Project Mobile Application Security Verification Standard (OWASP MASVS). This industry-standard framework outlines requirements and best practices for developing secure mobile applications, including those in the banking and financial sectors. By implementing the guidelines set by OWASP MASVS, we address various attack vectors, such as storage, cryptography, authentication, network communication, code quality, and protection against reverse engineering and tampering.
Internal Audits and Dependency Management
Before incorporating any dependencies, we conduct internal security audits to ensure their reliability. We utilize well-established and widely used libraries, minimizing the risk of potential vulnerabilities. Furthermore, we manually perform regular updates to keep our dependencies secure.
Secure Storage for Entropy
To protect the entropy used in our wallets, we utilize platform-specific encrypted key storages. For iOS, we employ KeyChain, and for Android, we rely on KeyStore. In the case of web extensions, we use Chrome Storage and IndexedDB. The retrieval of entropy from storage only occurs when necessary, such as during mnemonic export or transaction signing, and is promptly erased from RAM (Random-access memory) afterwards.
Limited External Content
To mitigate the risk of JavaScript/HTML injections and man-in-the-middle attacks, we prioritize a cautious approach by avoiding the loading or execution of scripts from external sources. This precautionary measure helps to minimize potential vulnerabilities. Moreover, we strictly retrieve content, such as currency logos and market data, from trusted sources to ensure their integrity and security. Additionally, we implement data validation procedures to verify the format of acquired data, thereby enhancing protection against cross-site scripting (XSS) attacks.
It is worth noting that the importance of these security measures has been underscored by past incidents, such as the attack on MyAlgo wallet, where a potentially compromised CDN API key was exploited.
Summary
While using a cryptocurrency wallet always carries inherent risks, transparency and open development can significantly strengthen security measures and encourage collaboration among experts and enthusiasts. For instance, an audit conducted by Least Authority revealed critical vulnerabilities in Atomic Wallet a year before it suffered a breach resulting in $100 million in losses. Timely resolution and open collaboration could have potentially prevented such an incident. By prioritizing security measures such as generating secure mnemonics, employing genuine random number generation, following industry standards, maintaining an open-source wallet core, conducting internal audits, securely storing entropy, and limiting external content, we strive to provide clients with robust and trustworthy cryptocurrency wallets.
Remember, no security system can be completely foolproof, but by prioritizing transparency, adherence to industry standards, and continuous improvement, we can minimize the risks associated with cryptocurrency wallet security and protect users’ valuable assets.